CompTIA Cybersecurity Exam Pro iOS
Elevate Your Cybersecurity Skills!
Introducing CompTIA Cybersecurity Exam Pro — your comprehensive app for conquering the CySA+ (CS0-003), PenTest+ (PT0-002), and CASP+ (CAS-004) certifications. Whether you're starting in cybersecurity or aiming for advanced skills in penetration testing and security analysis, this app has everything you need to succeed in the ever-evolving world of cybersecurity.
Master the essentials of threat management, vulnerability detection, penetration testing, and advanced security architecture through expertly designed questions that cover all key exam objectives. With detailed explanations for each question, you’ll understand the reasoning behind each solution, helping you build a deeper understanding of cybersecurity techniques.
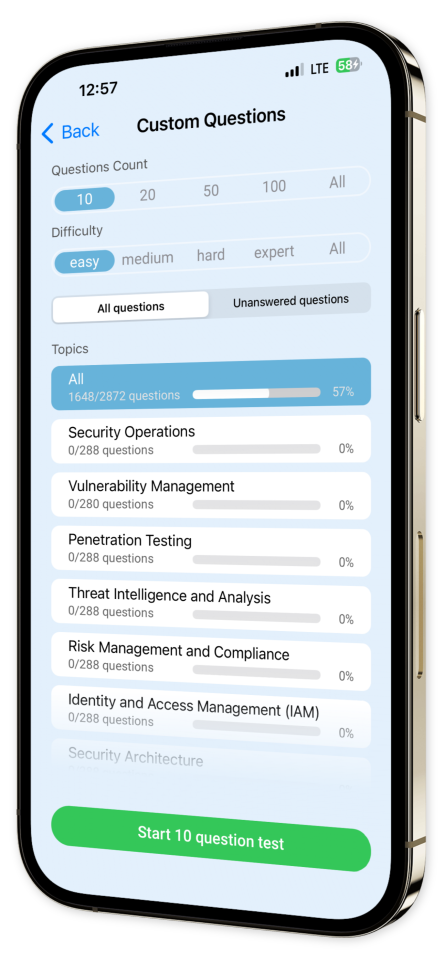
Customize your learning by focusing on specific areas, whether it's cybersecurity analysis, ethical hacking, or enterprise security solutions. Track your progress and compile a collection of challenging questions to ensure you're fully prepared for each exam.
Thousands of professionals have trusted CompTIA Cybersecurity Exam Pro to advance their cybersecurity expertise. Be part of the next generation of security professionals. Download the app today and get ready to tackle the CySA+, PenTest+, and CASP+ certifications with confidence!
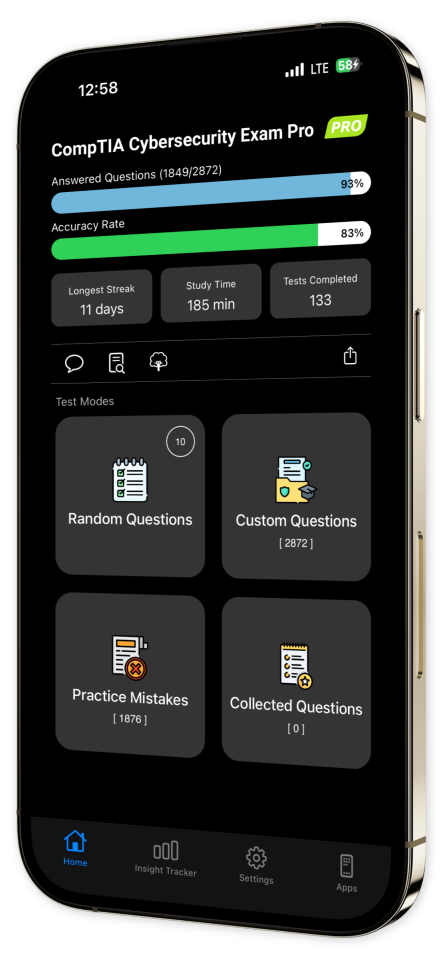
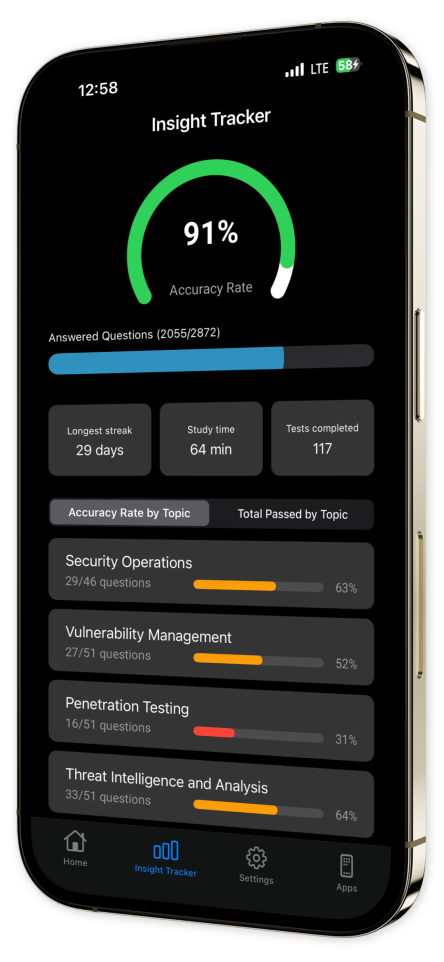
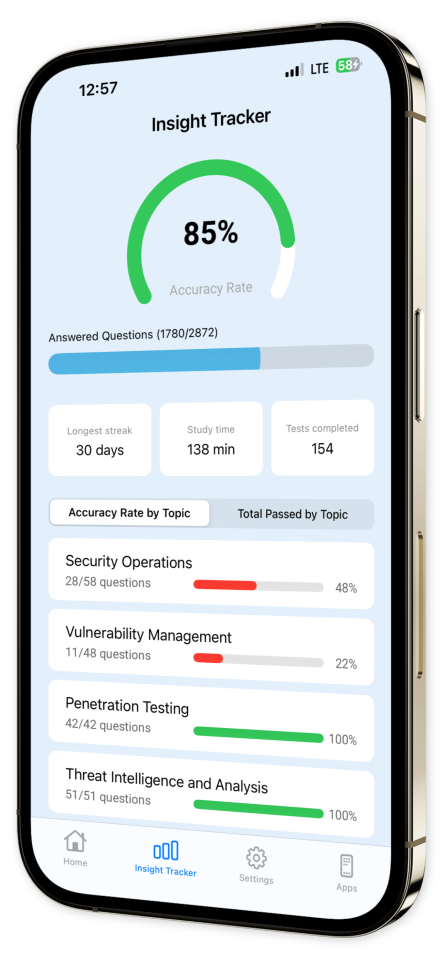
Content Overview
Explore a variety of topics covered in the app.
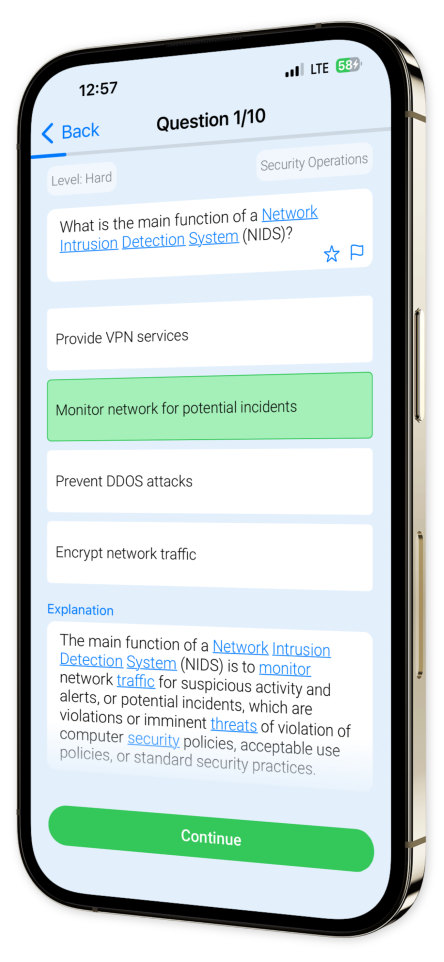
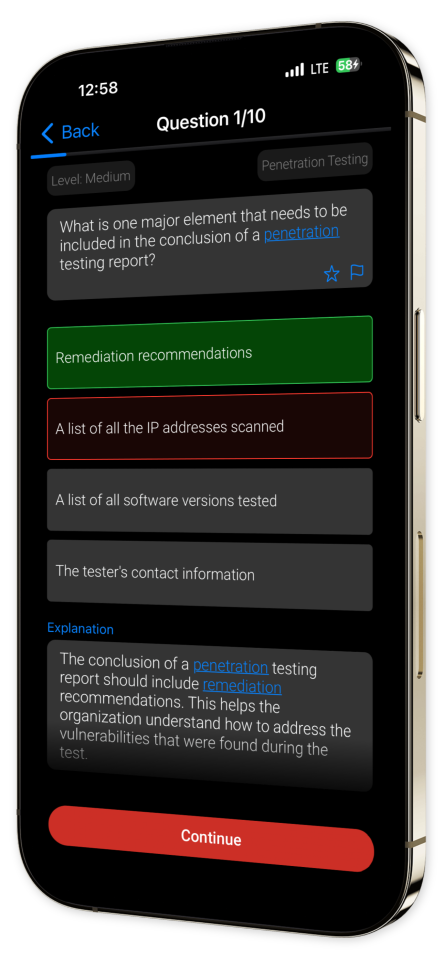
Example questions
Let's look at some sample questions
Which process improvement strategy focuses on continuous, incremental improvement?
LeanSix SigmaKaizenTotal Quality Management
Kaizen is a process improvement strategy that focuses on continuous, incremental improvement of an existing process.
What is the main advantage of using network scanning in asset discovery?
It can identify user accountsIt can identify vulnerabilities in assetsIt can identify hardware assetsIt can identify software assets
The main advantage of using network scanning in asset discovery is that it can identify hardware assets.
What is the purpose of a kill chain in cyber security?
To identify the type of malware usedTo predict future attacks and develop defensesTo map out the stages of a cyber attackTo understand the motives of the attacker
A kill chain in cyber security is used to map out the stages of a cyber attack from initial reconnaissance to exfiltration of data. This helps security professionals to understand the TTPs used by attackers and develop effective defenses.
Which of the following is NOT an element considered in a Business Impact Analysis (BIA)?
Recovery Point Objective (RPO)Recovery Time Objective (RTO)Maximum Tolerable Downtime (MTD)Annual Loss Expectancy (ALE)
Annual Loss Expectancy (ALE) is not considered in a BIA. ALE is a concept from risk analysis and it's used to measure the financial loss expected from a risk in a year.
Which of the following is NOT a typical requirement for incident reporting?
Time and date of the incidentType of incidentIdentity of the victimColor of the attacker's shirt
The color of the attacker's shirt is not a typical requirement for incident reporting. Incident reporting requires relevant information about the incident itself, not personal details unrelated to the incident.
Which access control model is most suitable for environments with high security requirements?
RBACABACDACMAC
MAC (Mandatory Access Control) is most suitable for environments with high security requirements. In this model, access is strictly controlled by a central authority and users cannot override the access controls.
Which of the following is NOT a key component of a PAM system?
Session managementPassword vaultingUnrestricted access for all usersAccess request management
A key component of a PAM system is not unrestricted access for all users. PAM is designed to restrict and control access, not to provide unrestricted access.
Which of the following is a disadvantage of biometric identity proofing?
It is easily replicatedIt requires the user to be physically presentIt is not unique to each individualIt cannot be changed if compromised
A disadvantage of biometric identity proofing is that it cannot be changed if compromised. Unlike passwords or security questions, biometric data is permanently associated with the user.
What does the principle of least privilege imply in the context of server hardening?
Every program and user should operate using the fewest privileges necessaryEvery user should have admin privilegesEvery program should have full access to the systemNone of the above
The principle of least privilege implies that every program and user should operate using the fewest privileges necessary to complete the task.
What type of vulnerabilities can Dynamic Application Security Testing (DAST) detect?
Vulnerabilities in the source codeVulnerabilities in the running applicationVulnerabilities in the network infrastructureVulnerabilities in physical security
DAST is designed to detect vulnerabilities in a running application that may not be apparent in the static code. It does not test source code, network infrastructure, or physical security.